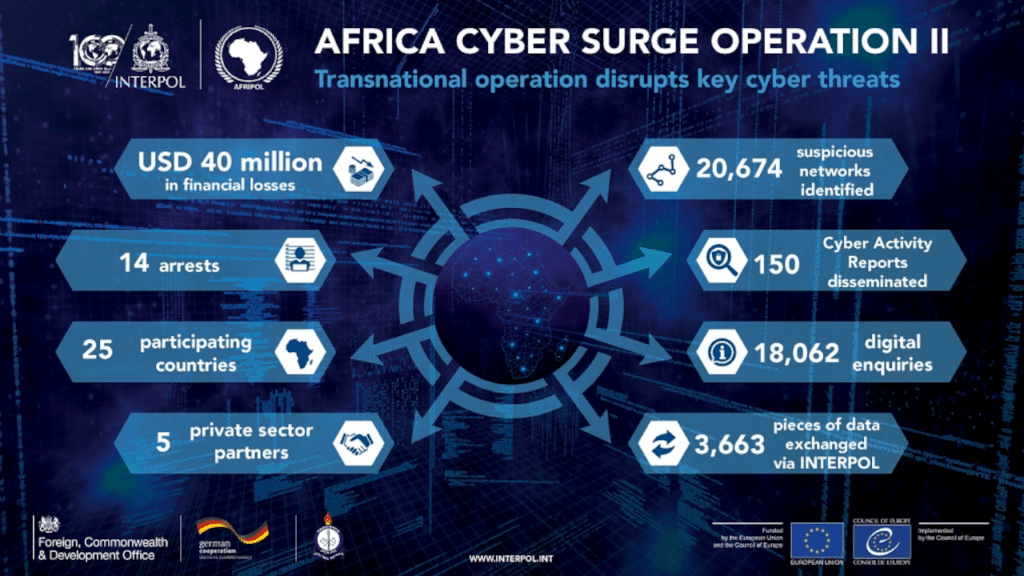
INTERPOL and AFRIPOL have coordinated an operation across 25 African countries that enabled investigators to arrest 14 suspected cybercriminals and identify 20,674 suspicious cyber networks, highlighting the surge in digital insecurity and cyber threats in the region.
The networks identified were linked to financial losses of more than USD 40 million.
The four-month Africa Cyber Surge II operation was launched in April 2023 and focused on identifying cybercriminals and compromised infrastructure. It was coordinated by INTERPOL’s Cybercrime Directorate, under the auspices of the INTERPOL Africa Cybercrime Operations desk and INTERPOL’s Support Programme for the African Union in relation to AFRIPOL (ISPA).
The operation sought to facilitate communication, provide analysis and share intelligence between countries, streamlining cooperation between African law enforcement agencies to prevent, mitigate, investigate, and disrupt cyber extorsion, phishing, business email compromise and online scams.
By leveraging actionable private sector intelligence, it underlined how cybersecurity is most effective when international law enforcement, national authorities, and private sector partners cooperate to share best practices and pro-actively combat cybercrime.
INTERPOL, AFRIPOL and private sector partners Group-IB and Uppsala Security provided on-the-ground operational support, sharing actionable intelligence leveraged throughout the operation.
Operational highlights
- In Cameroon, acting on a tip-off from Côte d’Ivoire, three suspects were arrested in relation to an online scam involving the fraudulent sale of works of art worth USD 850,000.
- Authorities in Nigeria arrested a suspect accused of defrauding a Gambian victim.
- Police in Mauritius arrested two money mules linked to scams initiated through messaging platforms.
- In Gambia, proactive measures and strong partnerships led to the take down of 185 Internet Protocols (IP) connected to malicious activities.
- Two Darknet sites have been taken down following actions by Cameroonian authorities.
- In Kenya, authorities took down 615 malware hosters.
Some 150 INTERPOL analytical reports providing intelligence and insight on cyber threats targeting specific countries were distributed to participating countries for investigative and disruptive actions during the operation.
Developed by INTERPOL based on information shared by partners Group-IB, Trend Micro, Kaspersky, and Coinbase, the reports contained information on:
- 3,786 malicious command and control servers
- 14,134 victim IPs linked to data stealer cases
- 1,415 phishing links and domains
- 939 scam IPs
- More than 400 other malicious URLs, IPs and botnets.
“The Africa Cyber Surge II operation has led to the strengthening of cybercrime departments in member countries as well as the solidification of partnerships with crucial stakeholders, such as computer emergency response teams and Internet Service Providers. This will further contribute to reducing the global impact of cybercrime and protecting communities in the region,” said Jürgen Stock, INTERPOL Secretary General.
The initiative highlighted the strong correlation between financial crime and cybercrime, allowing participating countries to expand their law enforcement response by adopting a “follow the money” approach.
It was also preceded by a one-week tabletop exercise in Tanzania on cybercrime and cryptocurrency investigations, equipping officials from 20 African countries with the knowledge and skills necessary for the successful execution of the operation.
“As digital systems, Information Communication Technologies and Artificial Intelligence grow in prominence, it is urgent that public and private actors work hand in hand to prevent these technologies from being exploited by cybercriminals. Coordinated operations such as Cyber Surge are necessary to disrupt criminal networks and build individual, organisational and society-wide levels of protection,” said AFRIPOL’s Acting Executive Director, Ambassador Jalel Chelba.
Africa Cyber Surge II was carried out with funding by the UK Foreign Commonwealth and Development Office, the German Federal Foreign Office and the Council of Europe.