One of the assignments that the security specialists at SWEPO Group carry out is security audits of companies’ security and security technical protection to analyse whether they have a level of protection adapted to the business. In this blog, the company advises on how to get the critical detection point right, starting with three key principles – Detect, Delay, Disturb.
According to SWEPO Group, in the vast majority of cases, the result is that the critical detection point is far too close to what needs to be protected for a resource capable of interrupting the attack to be able to reach the location and interrupt the attack. You as a company manager should not have to be able to calculate this, but your supplier of the security technology should be able to do so during their planning.
Simply put, the time to penetrate your business and reach what you want to protect needs to be longer than the time of detection + the time for an action, which can interrupt the attack, to be put in place.
First, ask yourself what the goal is with your physical and technical protection.
A simple, easy-to-remember formula can help security technology suppliers when designing your security protection:
- Detect a started and ongoing attack against what is to be protected
- Delay the attacker’s path to what is to be protected, and
- Disturb the attacker mainly through light and sound.
It is about technology to detect an attack using various detectors, sensors or camera surveillance with some form of analysis or sensor built-in.
By planning the security measures in different layers where you look at locks, doors, windows and walls, you can also strengthen the physical protection and make it more difficult for the attacker to get to what you want to protect.
Finally, we want to disrupt the attacker, either with the help of flash lights/strobes and sirens, or through fog generators that fill a room with a thick fog.
But that won’t be enough to protect your business. You need to use deterrence and interruption too. Deterrence, because the best scenario is that an attack on your business never happens. But then if you are attacked then you want to interrupt the ongoing attack before you lose what you’re trying to protect.
So how should you calculate your critical detection point?
The formula we use is TP > TD + TTA

This means that the time for penetration must be greater than time for detection and time for action, or time to act.
Explained in more detail, this means that the security technical and physical protection measures need to be designed so that an alarm is activated immediately when a potential criminal attack begins.
By placing the detection point before the first physical obstacle, you create an extended time for detection where resources can be directed to the location for a preventive purpose and prioritised when, and if, the attack begins. Already there, you have earned valuable time to be able to protect your business.
Rarely can you expect police action unless you can confirm an attack is in progress, so usually it’s a matter of how long it takes for an emergency responder to get to the scene. And you can easily check that time in your alarm call reports, where you see when the alarm has arrived at the alarm center, how long it took them to alert an emergency operator and how long it took them to get to the scene.
And the critical point of detection occurs just before the total response time (detection, response, arrival).
We analyse attack path and action time
SWEPO Group security specialists have a model for analysing and calculating attack paths and action time where we document the capacity and ability of the physical and technical security protection according to these principles during a site visit.
In its simplest form, we illustrate the model as follows;
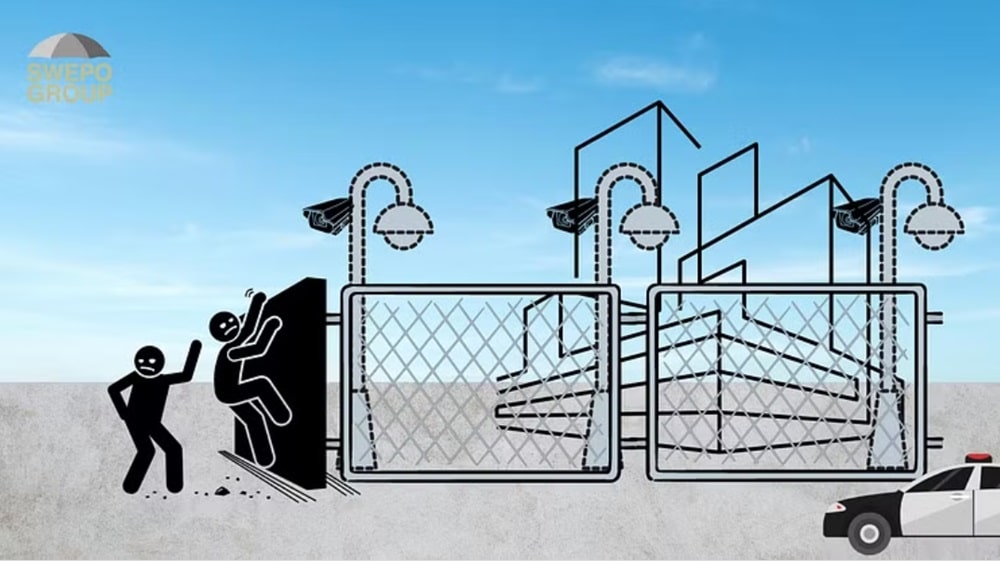
- The camera perceives a movement at the plot boundary and sends a signal to the alarm centre.
- It now takes five seconds for the person to cross the plot line and reach the fence.
- Climbing over a standardised fence takes 10 seconds.
- The attacker runs across the yard to your property and enters in 60 seconds.
The total time from attack initiation to penetration of what you want to protect is now just over 1 minute (75 seconds).
This means that the time for detection (+5 seconds) and the time for a resource to interrupt the attack should not exceed 70 seconds.
Are these unrealistic time intervals?
Studies show that it takes no more than five seconds to get over a standard fence, a so-called “Gunnebo fence”. If the fence is equipped with barbed wire, it can take up to 10 seconds to get over.
We can imagine that there is 300 metres between the fence and the property and the attacker can cover that distance in one minute, which would mean that the attacker could be anywhere within an area of 14.3 hectares – 141,300 square metres.
And time is the attacker’s best friend. Because with the same formula, the area to search corresponds to, already after three minutes, an area as large as 200 blocks in New York.
So then the simple question is – how often have your emergency responders been on site within 3 minutes of the alarm being triggered?
Is it useless to try to protect yourself then?
Absolutely not!
But, to avoid investing in physical and technical security solutions that become ineffective and costly, you should analyse what is worth protecting, and do your risk assessment first.
Depending on where in the country you operate, it is worth checking which security companies deliver emergency services in your area and ask you what their response time is in the event of an alarm call, and then plan your security protection based on those conditions.
For the sake of clarity, you need to know that the purchase, installation and maintenance of technical and physical protections that are able to prevent an attacker from getting in for 30 minutes will be both costly and will create obstacles and disruptions in your business for you and your employees.
Good security comes from well-balanced planning and risk analysis at a well-balanced cost that leads to reduced risks, increased security and secured profits.
For more SWEPO Group news, click here