Data Centres
ASSA ABLOY Door Group is highlighting the benefits of its highly advanced…
News
Datalec Precision Installations (DPI) is being recognised for its transparency on environmental…
News
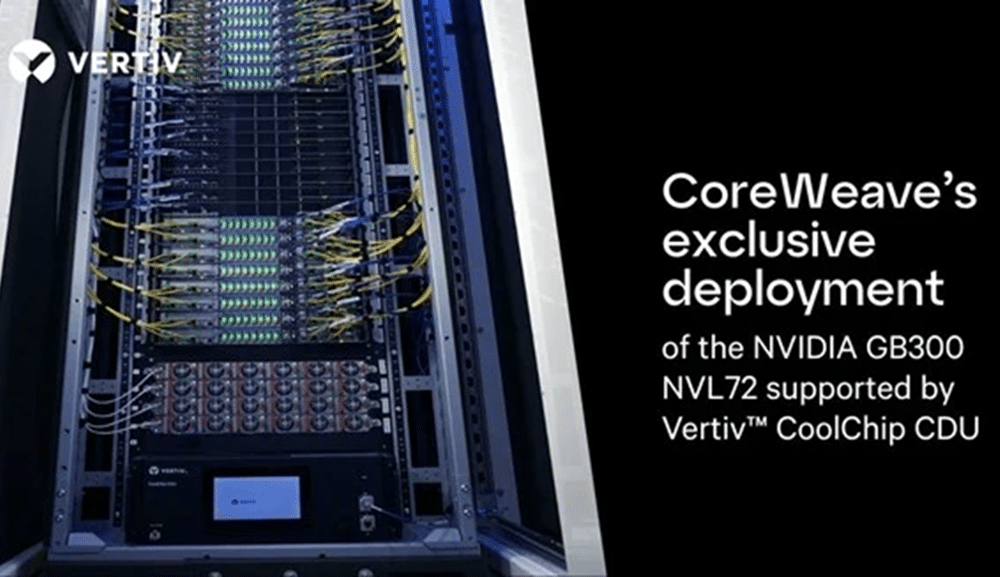
CoreWeave and its partners have delivered the world’s first…
News
dormakaba has acquired TANlock GmbH (“TANlock”), a leading German…
News
Datalec Precision Installations (DPI), a leading provider of world-class…
News
Load More