“Resilience is the ability to remain viable amidst adversity,” says Cloud Security Alliance in a new blog, which we’ve abridged here. Historically, says the author, we believed as an industry we could prevent incidents by the deliberate implementation of defenses. The few that got through would easily be addressed by the technical staff or would be covered by insurance (risk transfer). We also believed technical defenses were sufficient. After all, it is the digital assets under attack.
That is no longer the case. Incidents happen too often. Incidents are too disruptive, taking businesses offline for days, weeks, or even months. The impact to the business is too great. Too much to be covered by insurance. The long tail can last years with resulting lawsuits and loss of digital trust lasting years.
The malicious actors understand that many years of implementing technical controls have made these technical controls our strongest defense, so they go around them by attacking the people, the process, and the organizational dimensions. Most agree attacks on the human dimension (social engineering) are key to north of 90% of incidents. Some believe the number is 98%.
What to do? The solution is simple, but it takes execution. Instead of just focusing on technical defenses we focus on the technology, the people, the process, and the organizational dimensions through the entire cyber lifecycle of protecting, detecting, and recovering. NIST decomposes this into the five phases (Identify, Protect, Detect, Respond, Recover) in the Cyber Security Framework (CSF). There is no material difference in principle.
This is graphically represented:
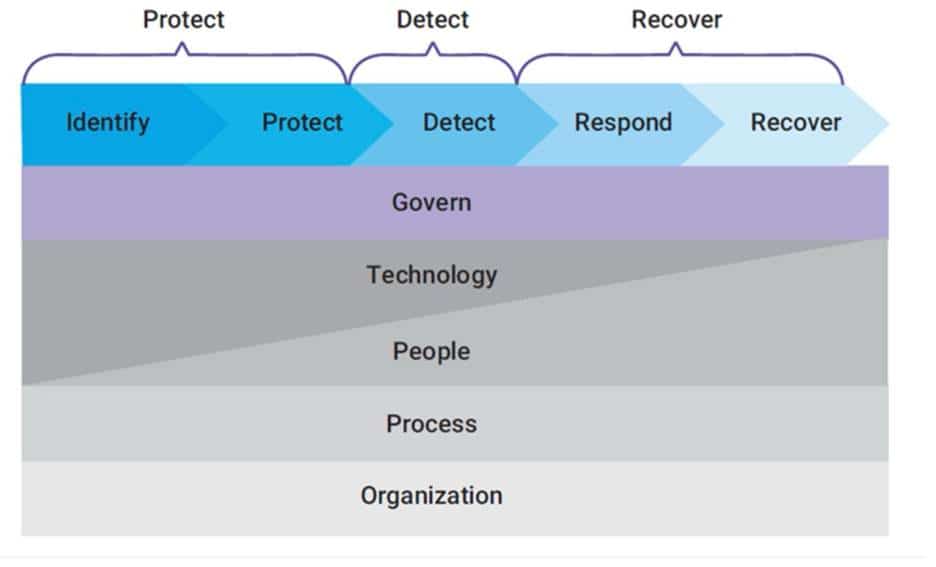
Resilience builds upon this in crucial ways. These include: No longer treating the delivery of products and services as either on or off like we did with Disaster Recovery (DR) and Business Continuity (BC), looking for alternate strategies, using of the Business Impact Analysis (BIA) to increase alignment between the business strategy, the security architecture, and operations, and focussing on external dependencies.
The blog also goes into detail about the role of Zero Trust, with a link to a quick review of the Zero Trust Guiding Principles shows an alignment between Zero Trust and resilience.
To read the full blog, click here
For more Cloud Security Alliance news, click here




