Jean-Philippe Deby, Director of Global Accounts at Genetec has shared his insightful commentary on the impact of GDPR five years on to Security on Screen and identified key areas for improvement within the physical security sector:
Coming from the public safety software industry, we’d often see companies treating privacy and security as a binary choice. I’m delighted to say the EU GDPR helped change that mindset, acting as a major catalyst for change in Europe and beyond.
Part of its legacy is that we now have explicit legislation for data and privacy protection in 137 countries around the world. It’s now much more accepted that privacy can be ensured without compromising security.
In terms of improvements, I am surprised how little attention has been paid to the specific challenges of ensuring compliance for the operation of video surveillance, access control and other physical security systems.
Any public or private organisations using CCTV to monitor public accessible areas should be concerned and operators need to focus on adopting privacy by design.
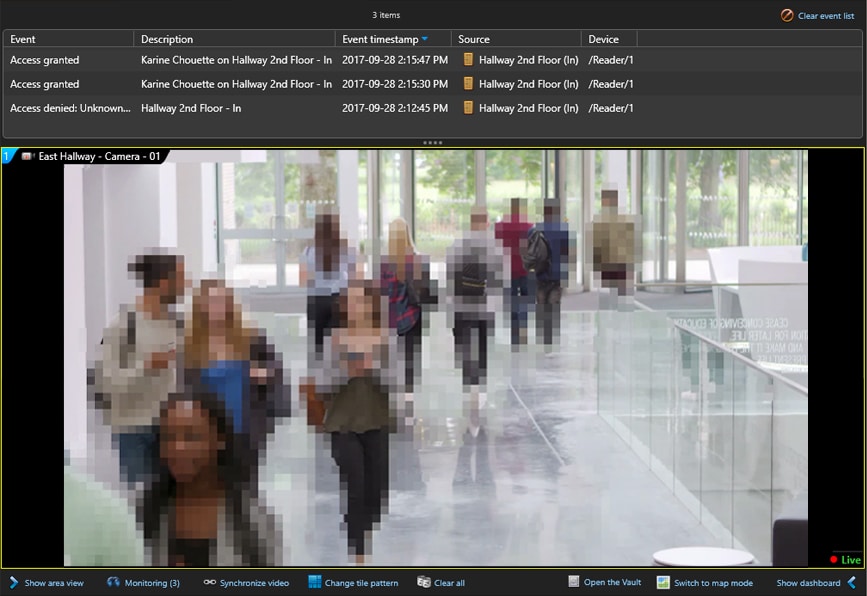
Under the terms of the EU GDPR, data that is anonymised or pseudonymised is classified as lower risk. The appropriate use of encryption and automated privacy tools is, therefore, a logical first step.
For example, video redaction that blurs out people’s faces in video, unless there is a legitimate reason to reveal their identity, can minimise the dangers of having security cameras deployed in public spaces.
Don’t forget, owners of on-premises video surveillance, access control or ANPR systems are responsible for all aspects of EU GDPR compliance, including securing access to the systems and servers storing the information.
However, by working with an approved cloud provider it is possible to offload some of these responsibilities and significantly reduce the scope of activities required to ensure compliance. It is also highly cost-effective.
Nevertheless, it is important to realise that it isn’t a full abdication of responsibility. You remain accountable for ensuring data is classified correctly and share responsibility for managing users and end-point devices.