Swedish security consultancy Swepo Security takes a deep dive into the world of cyber as part of European Cybersecurity Month, which aims to increase awareness of information security and cybersecurity issues, both among companies and private individuals.
Since 2012, the month of October has been the EU’s joint information security month (European Cyber Security Month) so this is a perfect time to explore the topic of cyber, and what it means. And we probably need to be reminded of the risks in our digitally connected life!
What is Cybersecurity?
But what exactly is Cybersecurity, and how is this different to Information Security? Is there a difference, or is it just different terminology?
In EU regulation 2019/881, cybersecurity is defined as all activities that are necessary to protect network and information systems, users of these systems and other affected persons against cyber threats.
Yes, but then what is a Cyberthreat?
We read further in the EU regulation and their definition of a cyber threat is a potential circumstance, event or action that can damage, disrupt or otherwise negatively affect network and information systems, users of these systems and other people.
Information security has a generally accepted definition in ISO 27000, which is described as “the preservation of the confidentiality, accuracy and availability of information, simply translated to only authorized persons, operations or processes may access the information (confidentiality), the information is protected against being intentionally/unintentionally changed or destroyed (accuracy), the information is available to authorized persons when it is needed (availability).
So, in summary, it can be said that Cybersecurity is about technical, physical and personal measures and solutions to keep our information protected from internal and external threats so as not to affect the company’s owners, employees, customers or other stakeholders from all forms of harm.
And information security is more about the overall framework that gives directives to who/whom are authorized to access which data, how data may be created, saved, changed or deleted and that the data is available to authorized persons without interruption of operations.
Cybersecurity for me privately
Attackers are good at profiling their targets, and adapt their attack methods depending on which group you belong to.
A common occurrence among the crimes targeting older people, is where the criminal calls the elderly person and pretend to be calling from the bank and claim that there is a problem with the account or that a payment has not gone through.
They ask the victim to open their BankID to identify themselves so they know they are talking to the right person, while the fraudster makes a login request to the bank. This shows a “normal” verification in BankID for the victim and after a short conversation they ask the victim to reconfirm in BankID and if the victim is not paying attention, they may have approved a loan or a transfer of their saved money to an account controlled by the perpetrator.
Another attack uses is carried out via SMS or email where the perpetrator claims to be from the police and claims to have noticed suspicious criminal activity in the victim’s surfing history. It might allude to child pornography crimes, or emails where you claim to have come across the user’s webcam and captured video sequences of when the victim satisfies itself and in both cases compensation is demanded, either in the form of a fine or by sending bitcoins so that the footage is not shared to your contact list.
Further common attacks on privacy include AI-powered phishing that attacks the victim’s email. Where possible, users should always enable two-factor authentication, never click on unknown links, and update their software on connected devices when notified.
IoT devices should be classified as a very likely attack surface because many manufacturers do not offer security updates. Change the default passwords, use passphrases and update software and firmware regularly.
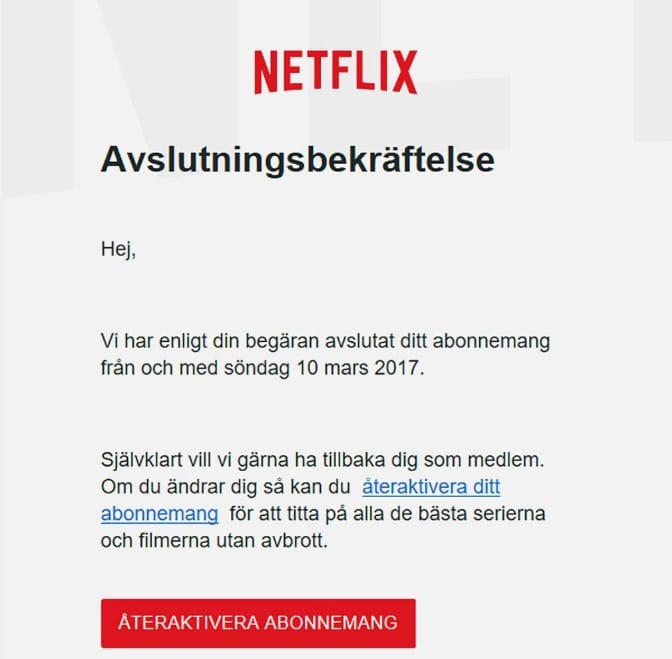
Imitation platforms
In early 2023, Internet security company F-Secure published a report showing that the most imitated social platform for spreading phishing threats was Facebook, while Steam was the most popular distribution platform for counterfeited PC games.
When it comes to streaming services, Netflix was the most used platform playing on our addiction to entertainment where a common scam is to notify the user that a payment has been declined and that new information is required which the perpetrators then use to access the account.
How do I protect my business?
At Swepo Security we know that the technical aspects of Cybersecurity can be extensive and complicated and we can’t explore too deeply here, however, a basic protection for companies is to invest in a firewall.
But beyond that, it’s a lot about keeping your employees aware of the risks in the digital environment, not only in the office but also outside and even on the move.
A cautionary example is not to use USB charging plugs in public places, but always use chargers with an electrical plug. The reason is so simple that you have no control over what is behind the outlet and they are rarely or never checked by the property owner and therefore become a great tool to gain access to your connected devices.
Do you want help with your cybersecurity and get tips and advice on how to protect yourself?
Book a free meeting directly with one of our Swepo Security safety coaches by clicking here.
For more Swepo Security news, click here





