Bernard Montel, EMEA Technical Director and Security Strategist, of Tenable gives an exclusive interview regarding the recent study entitled ‘Beyond Boundaries’ and suggests how organisations can prepare for cyber attacks more diligently.
The recent study of Beyond Boundaries, commissioned by Tenable and conducted by Forrester Consulting, says 55% of organisations are lacking in confidence in their ability to accurately analyse and measure their cyber risk – as we enter 2022, what predictions do you have surrounding organisations’ cyber risk analysis?
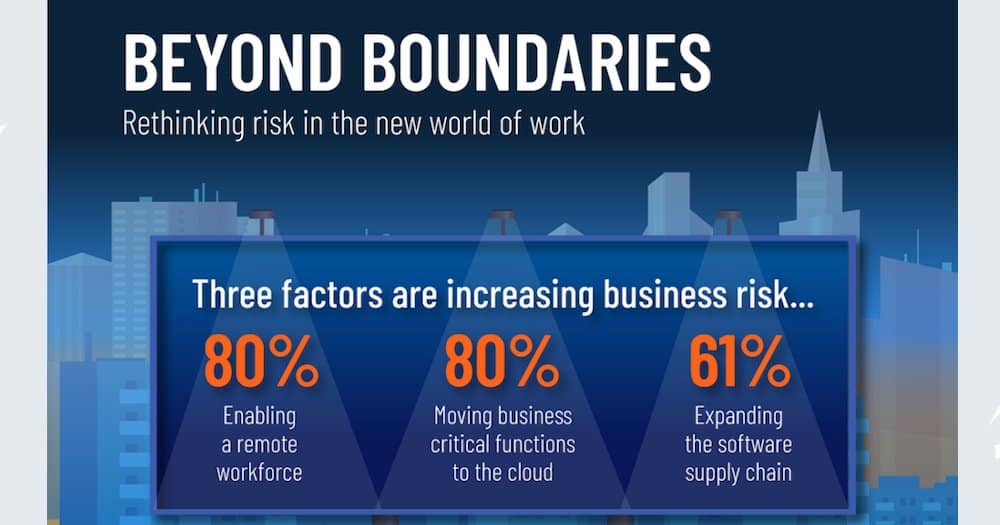
“The way we work has been evolving over the last decade as organisations embrace connectivity. However, this digital transformation was expedited in 2020 as the global pandemic dramatically and irrevocably changed the way we work. According to the recent Beyond Boundaries study, 70% of U.K. organisations support remote employees compared to just 31% prior to the pandemic. As organisations open their networks externally — whether it’s to accommodate a remote workforce, allow third party consultants access, or even remotely monitor a sensor on an oil rig in the Atlantic ocean — each connection complicates the infrastructure security teams need to monitor and assess.
“The tools and approaches organisations use to understand cyber risk don’t even work in the old world of client/server, on-premises data centres and a linear software development lifecycle where there is less complexity and more control over security. An asset is no longer just a laptop or server. It’s now a complex mix of digital compute platforms and assets which represent your modern attack surface, where the assets themselves and their associated vulnerabilities are constantly expanding, contracting and evolving – like a living organism.
“Effective risk management is built on a unified understanding of the entire IT/OT attack surface, which includes ICS devices, IT-based workstations on OT networks, IT networks and Cloud. This includes complete visibility, threat detection and mitigation, asset inventory, vulnerability management and configuration control, to maximise the safety and reliability of systems.
“By reducing complexity we can increase cyber risk analysis confidence.”
What would you say is the most pressing issue within cyber risk analysis? Is there a particular aspect that organisations need to be more aware of?
“A few years ago, the idea of crippling an organisation rendering it completely unable to function via a cyberattack was the storyline for numerous Hollywood movies. However, that fiction is today’s reality. Hybrid working environments are now the norm, critical functions are permanently housed in the cloud, services have been outsourced to third parties, digital divides between operational technology and IT systems have been torn down. While necessity drove these changes this highly dynamic environment has seen the attack surface explode with devastating consequences.
“That said, the fight isn’t all one sided. Security capabilities have also improved and the window between a threat actor compromising systems and security teams detecting the intrusion have reduced. Having determined that someone has accessed systems is just the first step, it’s also about ensuring that the damage that can be inflicted is also contained.”
What are the most effective ways to protect critical assets within an organisation?
“It might seem simplistic but it’s about cyber hygiene – pure and simple, do the basics and do them well. Organisations need a holistic view of what makes up their infrastructure. Knowing what’s there, its about determining what is critical for the organisation to function or pose the greatest threat if it is exposed. Knowing what you’ve got, the next step is determining ownership – who relies on those systems and data and how it is being accessed. This helps focus efforts on protecting these vital assets, services and data.
Having identified what is important, the next phase is determining the attack paths threat actors could utilise to target this and address them. Identify known vulnerabilities that threat actors are actively targeting and either patch or remediate the risk. Identify Active Directory misconfigurations that could allow privilege escalation attacks and tighten controls. That way, you close the windows threat actors look to climb through, remove the keys they can use to unlock secure areas, and stop them walking through the corridors and taking what they want.
As we adapt to a remote working lifestyle, is there any advice or suggestions you have to prepare for a potential cyberattack?
“In 2020, as COVID spread globally, many countries mandated employees to work from home where possible. To enable this, many organisations introduced working practices which inturn atomised the attack surface virtually overnight into myriad attack surfaces. Unfortunately for security teams, many found their security controls unable to meet this change in circumstance. Corporate endpoint devices dependent on perimeter-based security were taken outside the perimeter while unmanaged devices proliferated. The ability to holistically analyse this new borderless perimeter presented a challenge to define and address the risk introduced from a wide range of new attack paths through which to penetrate corporate networks.
“With the change to working practices unlikely to be revoked and hybrid environments becoming permanent, we will see organisations expand their management of risk in 2022 and beyond. Attack surface visibility has to become more complete – to include the cloud, remote devices, operational technology and Active Directory assets. Perimeter-based systems no longer apply, it’s time for a zero-trust approach.”