Manufacturing
Denrich Sananda, Senior Consultant, Arista Cyber, discusses the link between food safety…
News
SoS was shown the specialized medium to long-range camera offerings from Silent…
News
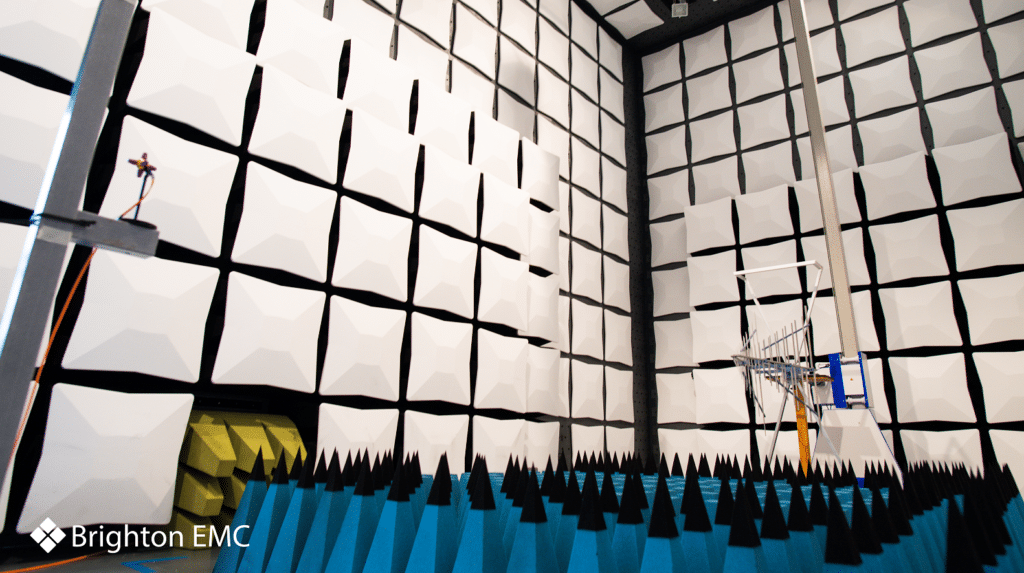
Brighton EMC is the new customer-facing brand for what…
News
Businesses in every sector face the challenge of operating…
News
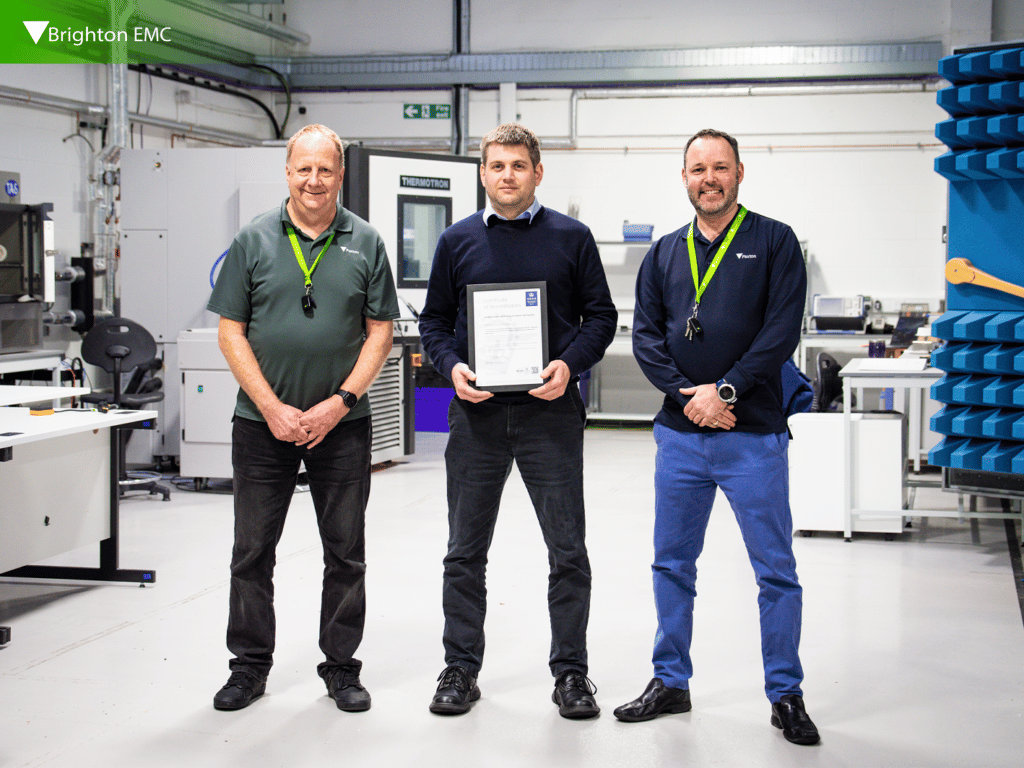
The Sussex-based security technology manufacturer Paxton has gained UKAS…
News
Load More